Protecting an organization's network infrastructure and making sure that their online services can always be accessed at any time is really necessary. Attackers are always developing new methods to circumvent conventional security precautions, which has led to an increase in the complexity of distributed denial of service assaults (DDoS). In order for enterprises to successfully combat these assaults, they need to keep up with the newest developments in DDoS attack methodologies and use proactive security solutions that can identify and mitigate these attacks in real-time. Organizations are able to reduce the effect of DDoS assaults and protect the integrity of their online operations if they form partnerships with skilled cybersecurity providers and adopt strong defensive mechanisms.
Introduction
Distributed denial of service, or DDoS, assaults have grown more common and dangerous in today's digital environment, posing a threat to businesses and organizations all over the globe. These assaults are aimed to flood a certain network or website with an excessive quantity of traffic, making it unavailable to those who have genuine reasons for attempting to use it. Attackers are always refining their strategies and coming up with innovative approaches in order to sidestep conventional security precautions. As a result, it is essential for businesses to keep abreast of the most recent developments in DDoS attack methodologies and to employ proactive security solutions that are able to identify and neutralize such assaults in real-time. Organizations are able to successfully reduce the impact of DDoS assaults and protect the integrity of their online operations if they form partnerships with skilled cybersecurity providers and deploy powerful defensive mechanisms.
What a DDoS Attack Is?
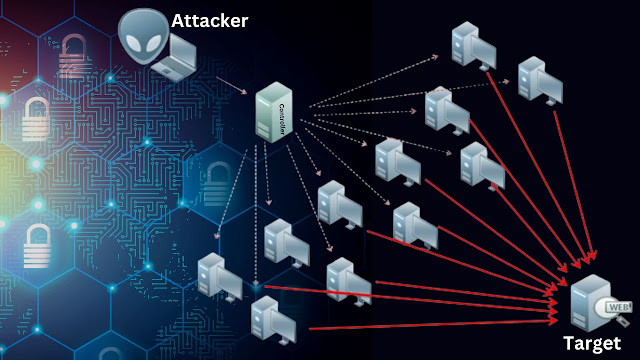
Distributed denial of service attacks, often known as DDoS assaults, entails flooding a target system or network with an excessive quantity of traffic in the hopes of making it incapable of performing normally or unavailable to users who are really authorized to use it. In most cases, these kinds of attacks involve numerous hacked devices coming together to create a botnet. The botnet is then managed by the attacker to bombard the victim with an overwhelming amount of traffic. DDoS assaults are carried out with the intention of creating financial losses, reputational harm, and possibly consumer discontent by disrupting the online services of the company that is the target of the attack.
The importance of analyzing patterns of DDoS attacks and identifying workable solutions
In order for businesses to keep one step ahead of hackers, it is essential for them to understand the tendencies of DDoS attacks. Businesses are able to design effective responses and enhance their cybersecurity infrastructure if they do an in-depth analysis of attack trends and detect developing approaches. Not only does the implementation of powerful DDoS mitigation solutions assist protect online services, but it also helps retain the confidence and happiness of customers. Because of the constantly changing nature of DDoS assaults, it is very necessary for businesses to make investments in preventative measures in order to reduce the possible dangers to their finances and reputation that are linked with these disruptive attacks.
Trends in Denial of Service Attacks
Over the course of the last several years, distributed denial of service assaults have gotten more complex and devastating. Because those that launch attacks are always refining their methods and plans, it is crucial for firms to remain current on the most recent developments in attack methods. The proliferation of Internet of Things botnets, as well as the growing prevalence of reflection and amplification assaults, are two examples of the changing threat environment that businesses need to be aware of in order to modify their cybersecurity measures appropriately. Businesses have the ability to keep one step ahead of would-be attackers and efficiently defend their internet infrastructure if they remain aware and take proactive measures.
An increase in the number and severity of distributed denial of service attacks
is yet another pattern that companies have to keep an eye out for. Attackers are using new strategies to launch distributed denial of service assaults, which have grown more common and sophisticated in recent years. These attacks aim to overload the servers of their targets and interrupt the internet services they provide. It is very necessary for companies to make investments in powerful DDoS mitigation solutions and test their defenses on a regular basis to guarantee that they can resist assaults of this kind. In addition, companies have to have incident response plans ready and waiting in the event that a successful DDoS assault is launched against them. This will allow them to swiftly restore their services.
Statistics and data illustrating the growth in the number of DDoS attacks
may function as a wake-up call for companies, urging them to take preventative actions to safeguard themselves from potential threats. A new analysis indicates that the number of distributed denial of service assaults (DDoS) has climbed by 20% in only the last year. This worrying trend demonstrates how urgently it is necessary for organizations to maintain vigilance and put into place appropriate risk mitigation methods. Organizations have a higher chance of successfully defending themselves against the ever-evolving dangers that face them and protecting their online presence if they keep abreast of the most recent developments in attack methods and invest in the appropriate technologies.
The frequency and scale of DDoS attacks are increasing. In 2022, there were over 10 million DDoS attacks reported, up from 7 million in 2021. The largest DDoS attack on record was 1.7 Tbps, which was launched against a gaming company in 2021. Recent years have seen a number of notable high-profile DDoS assaults including the one that occurred on Dyn in 2016, which caused major websites like Twitter, Spotify, and Reddit to become inaccessible to users. In 2018, GitHub was the victim of yet another big assault, which resulted in periodic disruptions that lasted for several hours. These occurrences serve as a warning that no company is safe from DDoS assaults and that even the most well-known platforms may be susceptible to being exploited by cybercriminals. It is imperative that companies draw lessons from these occurrences and take preventative measures to safeguard their infrastructure as well as their customers against the possibility of experiencing interruptions and financial losses.
The effect of the expanding Internet of Things (IoT) on the patterns of distributed denial of service attacks
The expanding Internet of Things (IoT) has had a substantial influence on the patterns of distributed denial of service (DDoS) attacks. The number of susceptible targets available to hackers has expanded significantly as a direct result of the exponential growth in the attack surface caused by the growing number of devices that are linked to the internet. IoT devices often only have rudimentary security protocols in place, which makes them an ideal target for botnets that are used in distributed denial of service assaults (DDoS). As the number of Internet of Things devices continues to expand, it is vital that businesses place a priority on the security of these devices in order to avoid them from being used as weapons in assaults in the future.
Changing methods used in distributed denial of service attacks
The evolving methods that are utilized in DDoS assaults are making the danger that is presented by Internet of things devices even worse. Hackers are always coming up with new techniques to take advantage of security flaws in these devices, such as using sophisticated malware or combining the processing power of several devices to launch assaults with more destructive potential. To effectively mitigate the risks associated with Internet of things devices and their potential use in distributed denial of service attacks, traditional defense mechanisms are often ineffective against these evolving techniques. As a result, organizations are required to invest in advanced cybersecurity solutions and stay updated with the latest threat intelligence.
Make the transition from volumetric assaults to more complex attacks on the application layer
Because of this trend, enterprises have been pushed to increase the security protections that are in place at the application layer. Instead of trying to overload the network with a vast amount of data, attackers are increasingly concentrating their efforts on finding and exploiting vulnerabilities in particular apps and services. Attackers are able to circumvent typical protection measures and obtain unauthorized access to sensitive data or disrupt key services if they focus their attention on the application layer. Organizations need to install modern intrusion detection and prevention systems that are able to recognize and block malicious traffic at the application layer in order to defend themselves against assaults that are becoming more sophisticated.
The emergence of attacks that use reflection and amplification
The introduction of reflection and amplification methods is one of the obstacles that must be overcome in order to successfully defend against these assaults. Because of these approaches, attackers are able to leverage the systems of innocent third parties to magnify their attack flow, making it more difficult to determine where the attack originated. Attackers may transmit a very modest amount of traffic that is subsequently mirrored and magnified by the targeted systems, which ultimately overwhelms the victim's network. This can be accomplished by exploiting weaknesses in systems that have been improperly designed. This necessitates that companies not only concentrate on the security of their own systems but also work together with other organizations to guarantee that possible sources of reflection and amplification are discovered and taken care of.
The use of botnets and several other malicious tools for distributed denial of service attacks
is yet another approach that attackers often use. Botnets are groups of computers and other devices that have been infected with malware and may be controlled remotely by a single hacker. An attacker may quickly overrun the capacity of the system and create disruption by coordinating a large number of these devices to deliver traffic to the network of the victim at the same time. In addition, attackers may use other malicious tools and tactics, such as IP spoofing, which involves misrepresenting the originating IP address of the attack traffic in order to make it more difficult to track it back to the real attacker. IP spoofing is just one example of a harmful instrument and technique that attackers may use. To successfully resist these dangers, it is essential for businesses to maintain current knowledge of the most recent security precautions and to work together with specialists in the relevant fields.
The reasons for distributed denial of service attacks
DDoS attacks may be carried out for a broad variety of reasons, including the pursuit of monetary gain, political action, or even just the simple desire to create havoc and disruption. Attackers may choose to target certain businesses or groups as a form of retaliation or competition in some circumstances. The growing availability of DDoS-for-hire services has made it simpler for people with less technological skills to launch assaults for personal reasons. This has led to an increase in the number of attacks. When companies have a greater understanding of the reasons behind these assaults, they are better able to predict them and defend themselves against them.
The acquisition of monetary benefit by means of extortion or ransom demands
is yet another typical justification for conducting an assault online. It is possible for hackers to breach the information technology systems of an organization and then demand a sizeable ransom in return for not disclosing sensitive information or regaining access to essential data. In recent years, this kind of cybercrime has witnessed substantial growth, with attackers going after both small enterprises and huge organizations. In order to reduce the likelihood of an organization being targeted by an assault motivated by financial gain, it is very necessary for that organization to have effective security measures in place.
The motivations behind activism and hacktivism
are also prevalent variables that contribute to the launch of cyberattacks on businesses. It's possible that some hackers are motivated by political or social reasons, and they utilize their talents to disrupt or expose injustices they see in the world. Defacing websites, releasing private information, and initiating distributed denial-of-service (DDoS) operations against government agencies or companies are all examples of the many types of cyberattacks that may be carried out. In light of the fact that these incentives are continuing to gain pace, companies have no choice but to not only concentrate their attention on financial motivations but also take into consideration the more comprehensive panorama of potential cyber risks they may face.
Targeted attacks on vital infrastructure Cyber warfare between states State-sponsored hacking and cyber assaults Competitive advantage or sabotage in commercial sectors Cyber espionage and theft of intellectual property Terrorism and political activity Targeted attacks on key infrastructure
Methods to Protect Against Distributed Denial of Service Attacks
To protect themselves against DDoS assaults, businesses may choose from a number of different mitigation strategies. Implementing effective network security measures, such as firewalls and intrusion detection systems, is one strategy that may be used to identify and prevent harmful traffic from entering the network. Additionally, companies may use content delivery networks (CDNs) to disperse traffic across numerous servers, making it more difficult for attackers to overload a single server. This can be accomplished by using CDNs. Partnering with a cloud-based DDoS protection provider is another option. These services may offer technical knowledge as well as the required equipment to absorb and filter out harmful traffic. Conducting vulnerability assessments and penetration testing on a regular basis may also help firms detect and repair any vulnerabilities in their systems that might be exploited by attackers. This can help organizations better protect themselves against cyber attacks.
Improvements to the infrastructure of the network
may also assist reduce the effects of distributed denial of service assaults. By putting in place powerful firewalls, intrusion detection systems, and load balancers, one may improve the efficiency with which network traffic is distributed as well as identify and prevent malicious activities. In addition, businesses may block known malicious IP addresses by implementing traffic filtering techniques such as rate limitation or blacklisting, which can restrict the amount of traffic originating from a single source. These strategies can be used to limit the quantity of traffic. These improvements have the potential to increase the overall resilience of the network infrastructure and decrease the likelihood that a DDoS assault would be effective.
As a conclusion, businesses need to understand the significance of recognizing the value of recognizing the significance of taking effective countermeasures and enhancing their cybersecurity infrastructure in order to prevent DDoS assaults. By making investments in strong DDoS mitigation solutions, companies can safeguard their online services, preserve the confidence of their customers, and guarantee the happiness of their customers. In addition, preventative actions are very necessary to play a significant role in limiting the possible financial and reputational consequences that come along with disruptive assaults like these. As a result, companies should make cybersecurity a top priority and take preventative measures to ensure the safety of their digital assets.





0 Comments